The sixth version of the most popular and popular operating system in the world of Android from Google, in addition to a number of various improvements, which highlighted in its announcement and launch, contains at least one interesting, and most importantly useful security option, which was not widely described.every year, phones and tablets are becoming more technically advanced and can perform more and more tasks. Initially, the most valuable data on the devices were SMS messages, contacts, less often – notes or files.
Table of Contents
ToggleHow does Factory reset protection work?
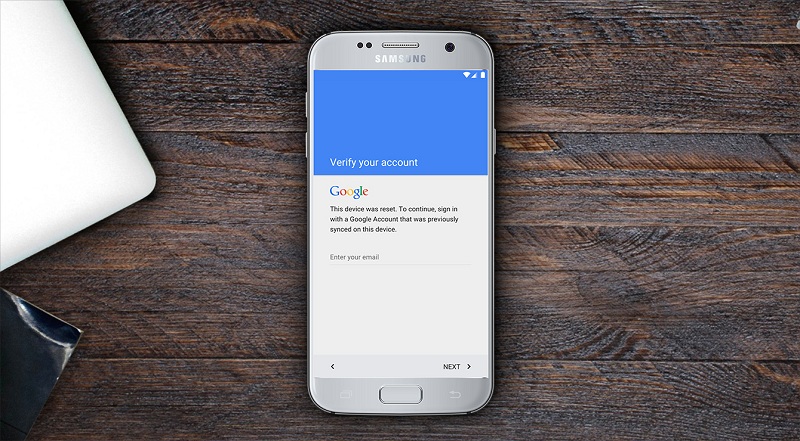
As it was written before, this function does not in any way complicate the life of the device owner, all you need to do to activate it on the example of Huawei’s Nexus 6P is to enter the Google account data into your phone the first time you start it, and also to set a password of any type for protection against unauthorized unlocking. Chic Nexus 6P from Huawei Separately it is worth noting that in devices of different manufacturers the implementation of the activation of this function may vary: so for Samsung based on Android 6 option is in the settings Samsung account. No less chic Samsung S7 Edge.
In order to understand how this will help in real life, let’s consider the option with the loss of a phone protected by factory reset protection and a password. So, the phone has an attacker, but it cannot pick up the password (of course, putting the password 1234 is clearly not worth it, if there is anything of value in the phone). If the purpose of stealing is data itself, the following steps are firmware recovery or using the software without erasing user data. The first fails because of the default bootloader, and in the second case, after turning on the phone will immediately promptly request access to the network and ask to enter the login and password from the Google account that were used before these operations, and until it is done, go through the phone setup is impossible.
Surely among the readers, there are those who are well versed in Android, and they certainly will say that you can flash custom, that is not the official software without Google services at all or make the full memory format before the firmware. In Google, foresee this, the first is again impossible with a closed bootloader, the second will not produce a result.
Thus, any action aimed at data reset or software change will result in the request for the password and mail from the entered account to the committed actions of the account.
How does it work?
When the conditions for factory reset protection activation are met, the data for testing is placed in the memory section, which is used to store the radio parts of the device. The trick of this move is that this area is a write-once memory. Thus, it is simply impossible to overwrite them or replace them without an extremely serious approach to the matter, which will consist in weeding out the memory modules and combating the new cryptography of Android. In other cases, an attacker will receive a phone without data that he can not even use.
iCloud activation lock against factory reset protection – who is better?
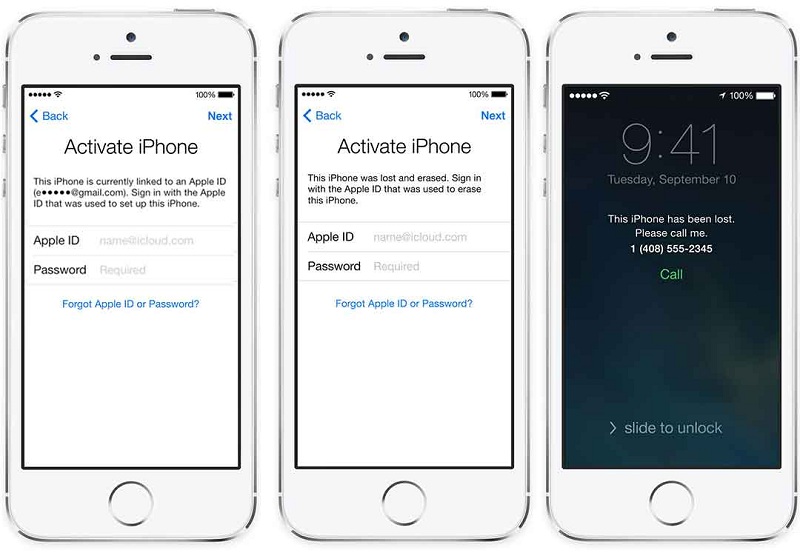
The pioneer of such a mechanism was Apple with iCloud activation lock, so without their comparison, the description would be incomplete, because the decision from Google came later, and certainly not without looking at the competitor.
- Initial setting and the need to set a password.
In the latest versions of Android and iOS, the creation of a password is requested by default, but it is not mandatory, so there is parity here.
- Explicit warning when resetting the device to the factory settings from the settings menu.
Here the Apple product explicitly asks you to turn off the option to prevent re-activation only when the firmware is not from the DFU via PC / MAC, otherwise, it is considered that only the owner of the device can enter the password and enter the reset menu. Android nowhere and does not warn that something is activated when resetting. In terms of security, this is a plus, in terms of surprises and usability – minus.
- Tips and ease of removing the lock by the owner of the device that knows both the username and password or their options.
IOS shows the start and end of the email address that was used on the device before the reset, Android does not. On the one hand, this is a plus for security, on the other – at least a tiny opportunity to remove the lock yourself, if the device was transferred to you for use, or it was a victim of experiments by children.
Of course, any or almost any protection can be hacked or circumvented, it is only a matter of the need and the resources to solve the problem. But it is worth remembering that when Apple entered this protection, the number of thefts of the iPhone went down sharply because the analysis of the phone on the details is too specific and non-trivial for the attacker. If the appearance of this mechanism after the greater distribution of Android M in the market will lead to the same trend – this will be a big victory.
For those who plan to give their Android M-based device for permanent use to children, a colleague, relatives or simply sell, it is worth remembering that in order to deactivate factory reset protection, it is necessary to delete accounts from the appropriate menu before resetting the settings, and also to clear data from the “security” menu “.
What in the end?
It is very pleasant that in Google, even if not publicly and with great fanfare (which would be logical, and quite justifiably), we seriously took up the aspect of protecting the personal data of users, of which the company’s services contain a huge number. Let FRP and not an ideal protection system, but for most situations of its capabilities, coupled with an emergency capability to remotely control the Android device, should be enough for most.